At TicketSignup, safeguarding your data is paramount. TicketSignup adheres to the Payment Card Industry Data Security Standard (PCI DSS) as the foundation for security across our entire platform. As PCI DSS evolves, so do our practices to ensure compliance and security. With the transition from version PCI v3.2.1 to v4.0, several significant updates have been introduced. These updates ensure TicketSignup remains in the forefront of payment security, and protecting customer data against evolving threats. Here is an overview of over 30 key changes.
Areas TicketSignup was Ahead of the Pack
There were a number of requirements that were introduced in v4.0 where TicketSignup was already compliant. We strive to continuously adjust our security posture to new threats. Here are some of the changes we already had in place:
- Upgraded handling of Card Data. TicketSignup does not store cardholder data, therefore these new requirements did not impact us. We encrypt card data and send it on to our payment partner for processing. This means cardholder data only resides where it needs to – at the payment processor.
- Web Application Firewalls – This is an industry best practice that has been in place at TicketSignup for years, now a requirement of PCI DSS v4.0.
- Protect passwords of system accounts – TicketSignup already had a key repo and procedures in place to satisfy this requirement.
- Quicker Response to Critical Failures – TicketSignup has always responded promptly to security threats, nothing to do here except continue to get better.
- Changes to lockout of login attempts – TicketSignup already exceeded this requirement.
- Endpoint Scanning Tools Must Now Authenticate with Application – The scanning tools we were using always had authenticated access to the application in order to do the deepest analysis.
Requirement Changes that Make Us Better
There were some processes and procedures we had in place that needed upgrading based on the new standard. Here is a rundown of the resulting improvements now in place to protect customer data:
- Greater accountability with defined roles and responsibilities for each of 300+ security requirements. Everyone at TicketSignup has a role in creating and operating a secure system, but only a few employees actually have access to these secure systems. This made meeting this requirement very simple for us and reduces our overall risk by keeping things tight.
- PCI DSS Scope Reviews – this is the process to review the scope of what is reviewed for PCI. TicketSignup decided a long time ago that the entire system would fall under the scope of PCI so that all data (not just credit card data) would benefit from the same high security. We moved the scoping exercise from annually to every six months to meet the new requirement. In addition we continue our in-depth quarterly internal audits of our security controls.
- Targeted Risk Analysis to determine the frequency of many of our activities. This was new in v4.0 and was a good exercise to ensure we were performing security tasks at the right frequency based on risk. We created or modified TRAs for 10 PCI requirements to meet the standard.
- Careful Tracking of SSL certificates. SSL certificates are what allow us to transmit data in an encrypted format across the internet. We manage SSL certificates for all of the domains we handle for our customers. TicketSignup already had a process to track SSL certificates, but added additional fields to our tracking system to meet the new requirement.
- Greater Focus on Protecting Against Phishing Attacks Phishing has become one of the leading ways bad actors compromise accounts. TicketSignup already implements email authentication protocols (DMARC, SPF and DKIM) to prevent attackers from impersonating our own domain. ( By the way, we also take care of this for our customers). However, we also put in place additional security products to identify phishing attacks and we continue to educate our customers and our employees on how to stay vigilant.
- System Account Reviews – TicketSignup already reviews developer accounts to all back end systems. With PCI v4.0 we expanded that to include every privilege in the security set as well as include system accounts (accounts that are not people, but processes that do automated work). With all of our production servers and all of the various access controls that we need to manage, there are thousands of controls to review. We will be writing automation software that increases the efficiency of these reviews in the coming months.
- Enhancements to our Secure Engineering Training Program. Security training across the company is constantly improving. In this round we upgraded developer training to include specific patterns applicable to our application as well as additional content for all employees around malware and protecting against phishing attacks.

New Payment Page Tamper Protection
Most of the requirements were enhancements to things we were already doing. However the most significant new requirement was the implementation of payment page tamper protection and alerting. TicketSignup previously protected against payment page fraud using a layered approach consisting of several different defenses (for obvious reasons, we would not want to disclose those here). PCI DSS requirement 6.4.3 and 11.6.1 introduced some very specific directives regarding payment pages. First, it required detailed inventory and management of all scripts on payment pages that are loaded and executed. It also required a mechanism to ensure the scripts were authorized and were not modified. Finally, it required a change-and-tamper detection mechanism to alert for any unauthorized modifications to the HTTP headers and the contents of the pages. The tricky part of that requirement is that it is required to be done at the endpoint (the consumer’s browser).
We looked at some commercial products to satisfy this requirement but found them to be incomplete and not cover all of the edge cases for a complex system like ours. We have over 30 different pages that accept secure payments and one to two thousands scripts that are involved in those pages.
Our Development Manager Ryan took a few months on his own to build a full blow application to cover these requirements. We think it is much more complete than most of the solutions we found in the market. This new application can spin up resources that act like consumer browsers and automatically catalog and inspect all of the pages that accept payments. It has the ability to take screenshots (and video capture) of the test if it is required for audit evidence. It runs regular automated inspections that are unattended but simulate a real user executing the steps from a browser. Of course it alerts our team of anomalies so they can be investigated. The system also steps the technical investigator through the review process and provides all of the data fields required to document the review, investigation and approval.
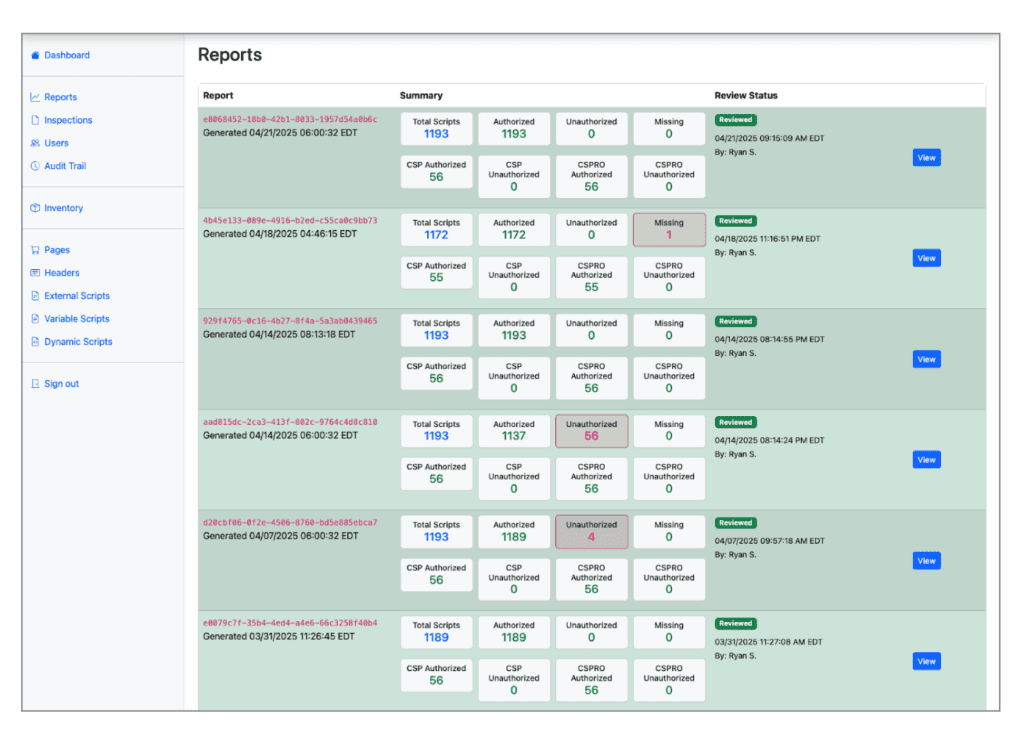
This new capability is an added layer on top of our existing processes that protect our customers from unauthorized scanning scripts that could intercept sensitive card data.
We Take Security Seriously
If you speak to security auditors, you will hear them tell lots of stories about companies that scramble to provide the right evidence at audit time or throw together missing documentation or procedures at the last minute to satisfy the audit. They pass the audit and the next 11 months they fall back to their old ways.
At RunSignup & TicketSignup, security isn’t about passing audits—it’s about consistently protecting our customers. We’re committed every day to maintaining the highest standards for your data security and peace of mind.
RunSignup / TicketSignup has been audited against PCI DSS v4.0.1. If you have questions about security or you require an AOC for your own security records, contact us anytime at info@ticketsignup.io.
